Quick Menu
Notes
HTTPS support in MyConnection Server (MCS) requires version MCS 10.1a or above.
As a best practice, this tutorial documents 4 steps to create the MCS certificate file using the Windows platform. The certificate file can be transferred and used with MCS on both Linux and Windows platforms.
Performing these steps on Windows is recommended even if MCS is installed on Linux.
Passwords used throughout the process must match and only contain letters and numbers. No special characters are allowed.
Overview
The 4 steps to enabling HTTPS/SSL in MCS are as follows:
- Create a combined SSL certificate that was provided by a certificate authority for use with MCS.
- Convert the certificate created in step 1 to an OpenSSL PKCS file.
- Convert the PKCS file into a Java Key Store (.jks) file for use by MyConnection Server.
- Configure MCS to locate and use the .jks file.
Passwords used throughout the process must match and only contain letters and numbers. No special characters are allowed.
Files created during the certificate build steps have been color coded for clarity of use.
Support: For help with the SSL certificate application process, review the troubleshooting section or send an email.
Step 1: Create the Combined Certificate File
A valid SSL certificate provided by the issuing certificate authority is required for this step. The certificate must consist of 2 files, for example yourdomain.com.crt and intermediateCA.crt.
Some certificate providers will provide a .PEM file option, for example yourdomain.com.pem. If a .PEM file is available, skip to Step 2.
The two certificate (.crt) files need to be combined together to create a single file as follows:
- Create and name a folder on the Windows desktop or other suitable location.
- Place the two certificate files to be combined in the named folder.
- Open a Windows command prompt and navigate to the named folder directory.
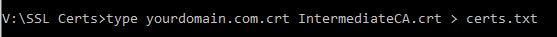
- Enter the command:
type yourdomain.com.crt IntermediateCA.crt > certs.txtto create the combined file.
Leave the command window open for continued use in Step 2.
Step 2: Install and Use OpenSSL to Package the Combined Certificate File
This step requires the OpenSSL package for Windows (scroll down to the Download Win32 OpenSSL section for download links) in order to convert the combined certificate file to the OpenSSL PKCS file format.
- If not already installed, download and install the full OpenSSL installer appropriate for the processor architecture required (32 bit or 64 bit).
- Once installed, locate the bin directory in the install folder. For 64-bit platforms this should be
drive:\OpenSSL-Win64\bin. - Add the bin directory path to the Windows PATH environment variable to allow OpenSSL to process from the open command prompt window.
- Enter the appropriate command line:
CRT method:
openssl pkcs12 -export -inkey yourdomain.com.key -in certs.txt -out certs.pkcs12PEM method:
openssl pkcs12 -export -inkey yourdomain.com.key -in yourdomain.com.pem -out certs.pkcs12

Step 3: Create the Java Compatible Key Store File (.JKS) to be Used by MCS
This step requires the Oracle Java keytool utility.
- If not already installed, download and install the Oracle Java JDK.
- Add the JDK bin directory path to the Windows PATH environment variable.
- Enter the command line:
keytool -importkeystore -srckeystore certs.pkcs12 -srcstoretype PKCS12 -destkeystore certs.jks -deststoretype JKS
V:\SSL Certs>keytool -importkeystore -srckeystore certs.pkcs12 -srcstoretype PKCS12 -destkeystore certs.jks -deststoretype JKS
Enter destination keystore password:
Re-enter new password:
Enter source keystore password:
Entry for alias 1 successfully imported.
Import command completed: 1 entries successfully imported, 0 entries failed or cancelled- When requested, enter a strong alphanumeric password for the destination (8 to 16 characters) and re-enter the same password for confirmation when prompted.
- When prompted for the keystore password, enter the same password used when creating the
certs.pkcs12file in Step 2, item 5. If these do not match, the certificate will be denied at run time. - The Java
certs.jksfile should have been created for use in Step 4.
Step 4: Configure MCS so it Can Find the JKS File
- Navigate to the
/MCS root/data/directory on the system where MCS has been installed. The key is valid to be used on Linux or Windows platforms. - For first time implementation, rename the
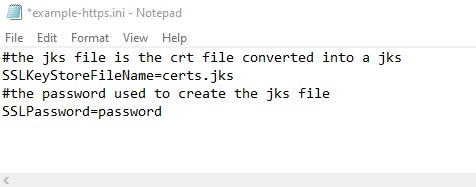
example-https.inifile tohttps.ini. - Copy the
certs.jksfile created in Step 3 to the/MCS root/data/directory. - Edit the
https.inifile and:- Amend the SSLKeyStoreFileName setting to reference the
certs.jksfile name. - Amend the SSLPassword setting to reference the password that was entered in Step 2, item 5.
- Amend the SSLKeyStoreFileName setting to reference the
The certificate configuration process is now complete.
MCS should be stopped and restarted to enable the SSL certificate. If a restart does not enable HTTPS, there may be an issue with the cert or JKS. Please review the troubleshooting section below.
Once enabled, only HTTPS traffic will be authorized and any user login requests initiated over HTTP will be automatically redirected to HTTPS. Port 80 is still required for redirects and support of high performance MCS hardware and software satellites which will continue to be authorized to ensure test accuracy.
Troubleshooting
- Passwords used throughout the process must match exactly and contain only letters and numbers. Special characters are not allowed.
- Verify that the password specified in the
https.inifile matches the one used for the certificate JKS file. - Ensure that the JKS filename specified in
https.iniis correct and that the file exists in the/MCS Root/data/directory. - Confirm that the installed Oracle Java JDK is the latest stable release. Issues have been reported with early access (EA) and release candidate (RC) versions.
Detecting the JDK Type Installed
Run the command below to check the Java version:
java --versionIf this does not explicitly state EA or RC, check the package manager:
Debian/Ubuntu:
apt list --installed | grep openjdkRed Hat/Fedora:
dnf list installed | grep javaArch Linux:
pacman -Q | grep jdkSome Java distributions (like OpenJDK) store version details in /usr/lib/jvm/:
ls -l /usr/lib/jvm/- Check the MCS console log located in
/MCS Root/logs/. If MCS encounters an issue verifying the certificate, details will be recorded there.

