Security Settings
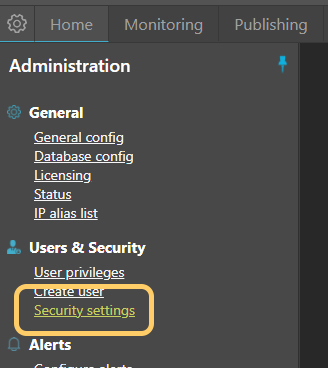
Security settings for MyConnection Server (MCS) can be found by clicking the security settings link in the Administration menu, as shown below.
The resulting page contains the following security settings.
Two factor authentication
Since version 11.3a, MCS has supported two factor authentication (2FA) via email.
2FA is an extra layer of security used to make sure that people trying to gain access to an online account are who they say they are.
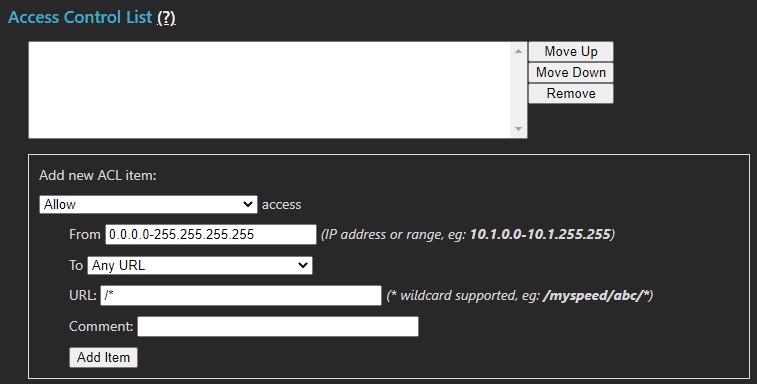
Access Control List
The ACL can be used to change access permissions to all, or part, of the MyConnection Server application. Restrictions can be applied by feature as well as by IP address including ranges and subnets. The list below defines what is permitted or denied. The ACL order defines rule-set priority, meaning that the first item to match is applied. If no item in the list matches, the URL is allowed subject to the MCS roles defined.
Warning: Be careful, the use of blanket rules that deny can block complete access to MCS.
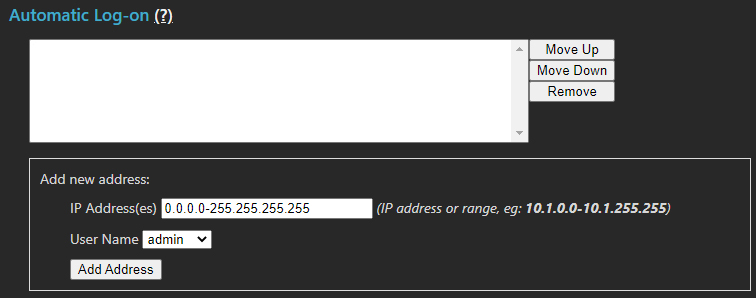
Automatic Log-on
Workstations can be automatically logged on based on IP address. Warning, using auto-logon for administrative privilege users is not advised. Note that workstations can still be logged in as a different user if extended privileges are required. The following list defines the IP addresses configured for auto-logon.
Security Headers
Security Headers allow the MCS administrator to add specific external headers to MCS HTTP transactions. Either add your own using the Custom Header text field or choose from a list of common headers. Warning, MCS is a custom web service application not a commercial web service such as IIS or Apache; adding headers may invoke restrictions that affect the overall MCS service delivery.
Cross Site Forgery
Cross-site forgery request attacks can allow a user to unwittingly submit a form or click a URL which is hosted on a malicious site, but which targets MyConnection Server. Enabling this option will require all future administrative access to be performed using forms submitted from MyConnection Server. If an MCS URL is referred outside of the MCS domain MCS will block the request as a CSFR violation and allow the requester to be redirected correctly.
Cookie attributes
Enable Secure: If MCS is deployed behind a proxy (for example, Apache) and the proxy serves it via https (the proxy does the encryption) MCS will add the 'secure' option to the 'Set-Cookie' header.
Enable httponly: Enabling this option will restrict Java applets from obtaining the MCS session cookies from the browser. If enabled it is important to ensure that the MCS applet testing option is enabled for the 'public' user, otherwise testing in the browser will be permanently disabled.
Proxy headers
Proxy services can interfere with the correct IP identification of clients requesting the MCS service. To ensure correct public IP user identification MyConnection Server provides the Proxy Headers to allow contents of an HTTP header to specify the public IP address if required.
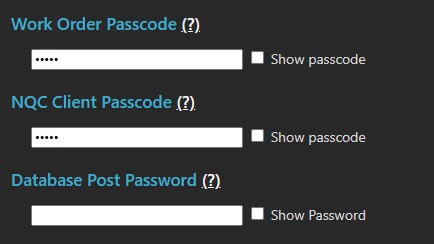
Token Passcodes (TPS)
Token passcodes are not passwords. TPS provides encryption services for satellite and other test protocol requests.
Work Order Passcode: Before any Satellite can initiate a test to an MCS, NQC Server or Satellite Access server, the Work Order must first authenticate the work order passcode.
NQC Client Passcode: Licensed NQC client Apps for mobile phones and tablet platforms including iPhones, Android, Windows* phone (*deprecated) are required to authenticate using the NQC client passcode.
Database post password (deprecated): Replicating MCS database results to another MCS will require the database passcode that is assigned to the receiving MCS.
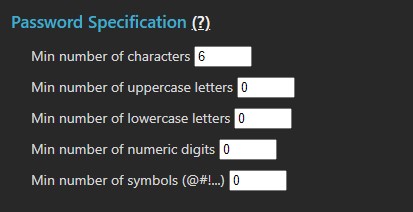
Password Specification
User password rules define the complexity rules for all user passwords in MCS. These rules do not apply to MCS passcode tokens listed above.
Route testing (IPV4 only, deprecated)
IP rules define the IP addresses that cannot appear within any route table or additionally, be allowed as a route destination. Enter one IP per line or an IP range, for example,10.0.0.0-10.255.255.255.
Custom alias names can also be declared for Specific IP addresses in the field below. The declaration form is IP= <alias name> For example, 10.0.0.0 = myprivate_server.